Cybersecurity Maturity Model Certification (CMMC)
- CMMC (V 2.0) – NIST SP 800-171 and NIST SP 800-172
- Cybersecurity Maturity Model Certification (CMMC) 2.0 Update
- Click For A FREE CMMC Overview
ATTENTION SUPPLIERS TO THE DoD:
In the near future Suppliers to the Department of Defense will be required to seek CMMC.
The CMMC is the accreditation body that certifies third party assessment organizations referred to as C3PAO’s. These organizations will facilitate the assessments.
 This set of requirements has been developed to standardize and protect Federal Contract Information (FCI) as well as Controlled Classified Information (CCI) developed, maintained or supported by the Defense Industrial Database (DIB). It is anticipated that by RFP by the DoD will include a specific CMMC level as a pre-requisite to any new contract awards.
This set of requirements has been developed to standardize and protect Federal Contract Information (FCI) as well as Controlled Classified Information (CCI) developed, maintained or supported by the Defense Industrial Database (DIB). It is anticipated that by RFP by the DoD will include a specific CMMC level as a pre-requisite to any new contract awards.
Effective January 2026, all new DoD contracts may contain the CMMC requirement.
The framework has three elements:
- Tiered Model: CMMC requires that entrusted companies implement security standards at progressively advanced levels, depending on the type and sensitivity of the information. This also sets forward the process for information flow down to subcontractors.
- Assessment Requirement: CMMC assessments allow the DoD to verify the implementation of cybersecurity standards.
- Implementation through Contracts: Once CMMC is fully implemented, DoD contractors that handle sensitive information will be required to achieve a particular CMMC level as a condition of contract award.
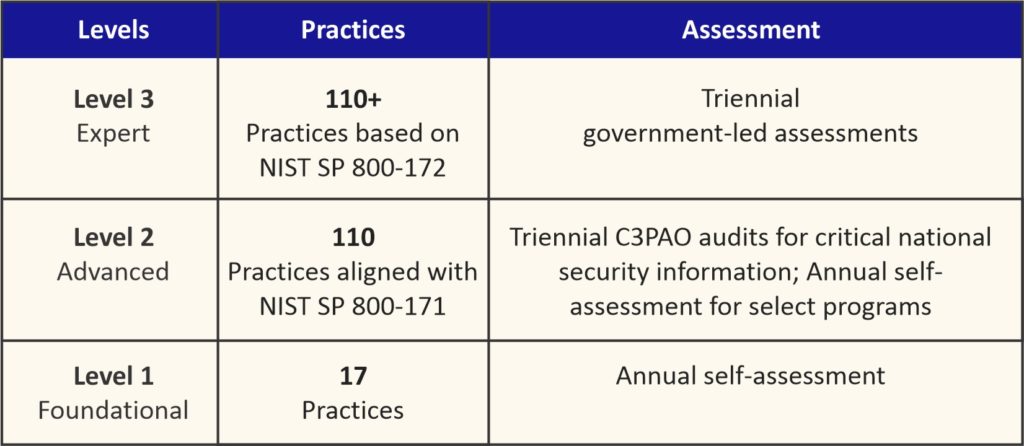
There are three Levels of Security Practices. Each Level will include a specific number of Practices.
- CMMC Level 1 – Foundational: This is the considered Basic Safeguarding of Federal Contract Information or FCI. Level 1 focuses on basic cyber hygiene practices specified in 48-CFR 52.204.21. There are 17 practices from six domains at this level. Annual self-assessment is required.
- CMMC Level 2 – Advanced: This level requires an organization establish and document practices and policies. Level 2 focuses on the protection of Controlled Unclassified Information or CUI. There are 110 Practices included at this level, derived from NIST SP 800-171. DoD contractors that handle sensitive information will be required to have Triennial third-party assessments for critical national security information or Annual self-assessment for select programs.
- CMMC Level 3 – Expert: This level requires an organization establish and document practices and policies. This level includes all the Level 2 practices and additional controls selected from NIST SP 800-172. The framework and assessment criteria document are under preparation. This level requires Triennial government led assessments.
Perry Johnson Consulting has Information/Cyber Security Consultants to assist in in meeting the criteria and preparing an organization for certification.
Following are the suggested implementation steps:
- Select a reputable consultancy partner like PJC to guide your certification project
- Perform gap assessment against the intended security level
- Awareness training of CMMC
- IT asset inventory and classification of assets
- Define the asset category in the Asset list and the network diagram
- Prepare documentation (Policies, Procedures, WI, Plans, etc.)
- Perform risk assessment/evaluation/risk treatment
- Selection of practices for identified risks
- Prepare a system security plan and define asset category
- Implementation of all controls to the intended level of certification
- Implement measurements and monitoring
- Analysis and evaluation of monitoring and measurement results
- Train internal auditors
- Perform internal audits and capture levels of practices
- Report levels to top management and review for changes
- Selection of third-party assessment organizations approved by CMMC AB (Accreditation Body)
- Pre-assessment
- Corrective action
- Assessment by the selected third-party assessment organization
- Corrective action for the identified deficiencies, if any
- Certification
Allowance of POAM’s and Waivers
Contracting officers can use normal contractual remedies to address a DIB’s contractor’s failure to meet their cybersecurity requirements after a defined timeline.
POAM’s may be allowed for certain non-critical controls.
Waivers will be allowed on a very limited basis, accompanied by strategies to mitigate CUI risk.
PJC will post updates as they are received.
For more information on CMMC or other Information Security Standards such the ISO 27000 series, contact PJC.

 "We are proud to provide services to the U.S. Government!"
"We are proud to provide services to the U.S. Government!"
